Edge AI face detection and recognition system
Robust solution for people identification, queue management & improving security in commercial facilities and public transportation.
The idea behind our solution
The facial detection & recognition algorithms and attendance systems have been widely known by entrepreneurs, open source contributors, and end-users familiar with mobile Face ID technologies. However, there are still business cases not covered by commonly available solutions.
What challenges do you want to overcome?

Do you want to replace RFID cards or fingerprint readers with a touchless technology?

Are you looking for a reliable system for automatic and contact-less authentication?

Do you want to increase passenger or employee safety at a managed facility?

Do you need to reduce delays from cloud processing or large file transmission?

Or are you facing other challenging issues that can be solved with edge computing and AI?
Contact us to discuss a customized solution
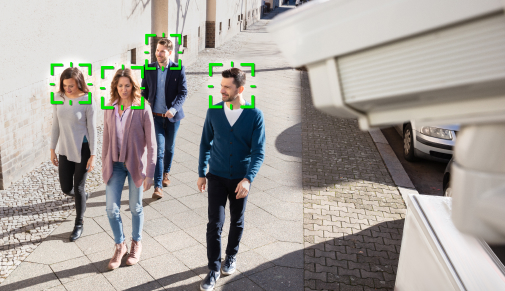
How does it work?
Want to see it in action? Check out the movie and contact our sales to request PoC.
Common business scenarios
Facial recognition for detecting employees
Identification of factory workers during shifts exchange and recognizing corporate employees at peak hours to prevent long queues.
Increasing staff safety
Replacing manual identity verification with a reliable solution that automatically recognizes authorized individuals.
Increasing staff safety
Replacing manual identity verification with a reliable solution that automatically recognizes authorized individuals.
Queue & waiting time management
Generating savings for the company with better time management of employees waiting in line for authentication to start a shift.
Preventing identity theft in transportation
The system prevents security violations and frauds, detecting people using a stolen ID card or an unauthorized ticket discount.
Preventing identity theft in transportation
The system prevents security violations and frauds, detecting people using a stolen ID card or an unauthorized ticket discount.
Solution powered by Edge AI computing

Edge AI computing
Facial detection & recognition system works on our custom-made Raco Edge AI Gateway. All operations are carried out on the device without the need for cloud processing. Raco has a built-in camera and can be enhanced with any other model connected via CSI or USB ports.
Main benefits
Quick operation
Our solution is fast and reliable – an authentication and detection process takes milliseconds.
Smart system
The system adapts to changes in appearance, recognizing a person wearing glasses, a hat, or a new hairstyle.
Time efficiency
Adding new people to the register is quick, requiring taking only a few photos to train the AI model.
GDPR compliance
There's no need to store sensitive data – the system can operate on the device, and the identification is fully anonymous.
Easy integration
Integration with external systems is possible using API and network connection through Ethernet, Wi-Fi, or LTE.
Technical aspects - types of cameras

Attended access
For face recognition, we can apply a standard camera used for monitoring facilities. Such a device, however, doesn’t recognize whether the image is three-dimensional or flat, which means that the system won’t prove effective in all security-related situations.
Advantages:
- Cheaper equipment
- Faster deployment
Unattended access
For a fully autonomous system, we need an infrared-based solution similar to those used to unlock a smartphone. The AI algorithm recognizes a real, three-dimensional face & illuminates it with infrared light that is invisible to the human eye.
Advantages:
- A safer solution
- More challenging to trick than a device that doesn’t recognize image depth
- Gatekeeper supervision isn’t required
Required equipment:
- IR illuminator – a small lamp that emits infrared light – to illuminate the entire face
- IR camera, which will verify what the illuminator has displayed and pass this information to the Edge-AI model, which will determine if we are dealing with a real face
Photos taken with an IR camera at all stages of recognition using a smartphone – the process takes about 1 s

From left:
- a standard image seen with an IR camera, image seen without the use of an illuminator,
- an illuminator lights up the entire frame (just like a flash when taking a photo),
- an illuminator throws randomly scattered “dots” on the frame,
- an illuminator throws random “patches” on the frame.
Contact us to discuss a customized solution
How do we work?
Gathering requirements
As an authorized Raspberry Pi Approved Design Partner, we have the necessary expertise to provide IoT technology consulting and deliver a tailor-made solution to meet specific customer needs.
Setting project starting points
An AI model needs to be trained with customer data, according to the principle – the better the training data, the better the model performs. The final solution’s effectiveness is determined by the environment, lighting, and how data is sampled for AI training.
Hardware selection
Each project is priced individually after the workshop. Developing a ready-to-use solution requires preparing a custom AI model and selecting the right hardware, choosing from Raco Edge AI, NVIDIA Jetson, or others.
The process of creating a custom-made AI model
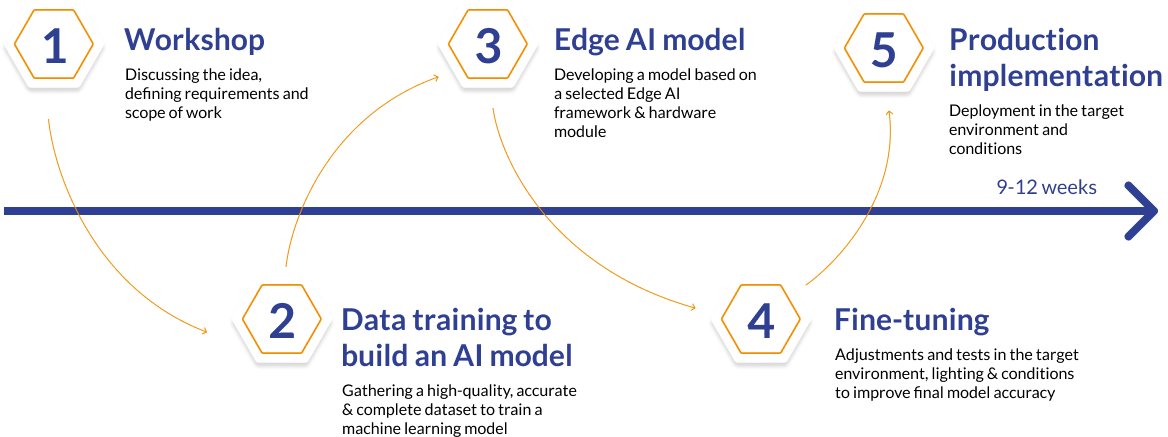
The process of creating a custom-made AI model
9-12 weeks
Workshop
Discussing the idea, defining requirements and scope of work
Data training to build an AI model
Gathering a high-quality, accurate & complete dataset to train a machine learning model
Edge AI model
Developing a model based on a selected Edge AI framework & hardware module
Fine-tuning
Adjustments and tests in the target environment, lighting & conditions to improve final model accuracy
Production implementation
Deployment in the target environment and conditions
Let’s stay in touch
Tell us about your IoT project and we’ll get back to you shortly.
Talk to our expert

Paweł Skiba
IoT Solution Architect